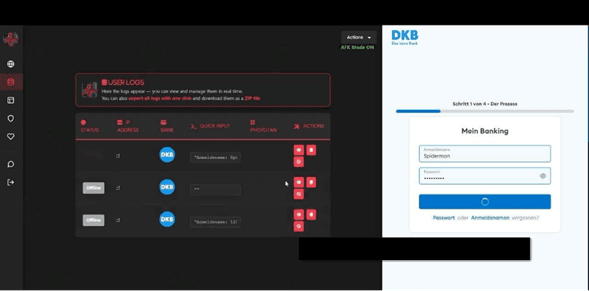
The Spiderman phishing kit is swinging into the cybercrime world, and this version is giving spider power to amateur hackers and pros alike.
A phishing kit is a toolkit for hackers to impersonate websites, email domains, and legitimate businesses to dupe users into sharing their login credentials and two factor codes and software and crypto keys.
What Makes The Spiderman Kit Different
Traditional phishing often relied on crude fakes and delayed exploitation. Kits like Spiderman are so named because of their realism, speed, and deceptive potential. They are illegal, of course, so don’t buy one!
The “Spider-Man” phishing kit includes templates impersonating major European banks, crypto platforms, and payment services and is designed to be nearly pixel-perfect, updating as fast as target platforms adjust their login flows. From an attacker dashboard, hackers view sessions in real time, harvest credentials, and intercept MFA codes as the victim tries to log into their account.
The Message for Business Leaders
The moral of the story is simple: someone in your organization will get phished. These AI-enabled phishing kits like Spiderman make that outcome more likely, even for organizations that believe they are “doing the right things.”
The question is not whether you can block every attack. The question is whether your organization is built to:
- Reduce the likelihood of compromise.
- Contain the blast radius when it happens.
- Prove you were prepared in the event of a challenge from your insurer, lawsuit or liability claim.
”Good intentions” do not matter. Evidence does.
Why “After the Click” Determines the Outcome
Modern phishing is no longer a simple email problem. It is an access problem, an identity problem, and an operational readiness problem.
When an incident occurs, your next steps determine whether it becomes:
- A contained credential reset, or
- A multi-day disruption involving lateral movement, data exposure, vendor notifications, and legal/insurance escalation.
And if cyber insurance becomes part of the recovery plan, documentation and defensibility can determine whether a claim is supported or challenged. If the insurance carrier starts asking hard questions, you need to show controls were in place before the incident, in use, and enforced, or you are effectively uninsured.
BTI’s recommendation: do not rely on Cybersecurity “products” or do it yourself protection.
BTI helps organizations reduce phishing risk and improve outcomes when phishing succeeds.
Our approach prioritizes:
- Security readiness you can prove (policies, training, documentation, evidence trails)
- Containment and response discipline (plans, escalation, multi-layer security, technical controls, operational playbooks)
- Integrated monitoring and oversight so your environment is not a collection of disconnected tools.
If you would like BTI to review your phishing readiness, incident response posture, and documentation defensibility, we can help you identify gaps quickly and prioritize fixes that reduce risk and strengthen your cyber insurance position.
Good Intentions Don’t Protect Your Business. Evidence Does.
If you’re not sure your organization could defend its phishing response to an insurer, auditor, or legal team, it’s time for a review.