Honeywell CCTV Critical Vulnerability (CVE-2026-1670): How to Prevent Camera Takeover

Most organizations still treat cameras and door systems as “facility technology.” Modern CCTV systems are IP endpoints that live on your network, share routes with business applications, and often have remote access paths that bypass the controls you enforce elsewhere. A new critical vulnerability affecting multiple Honeywell CCTV products is a reminder that physical security […]
IT System Integration Services Explained: Benefits & Best Practices

Organizations today rely on dozens of applications, platforms, and data sources to operate. When these systems don’t communicate effectively, the result is fragmented data, manual work, and operational inefficiencies. IT system integration services address this challenge by enabling different systems to work together as a unified environment. This BTI Communications Group guide explains what is […]
Success Story: How BTI Unlocked 80% More Performance from a Misconfigured Meraki Wi-Fi Network

A mid-market organization was running its Meraki Wi-Fi at just 20% of its potential. BTI corrected key misconfigurations, restored the 6 GHz design, reduced interference, and delivered high-performance Wi-Fi without new hardware.
Why Siloed Security Fails Compliance Audits in 2026
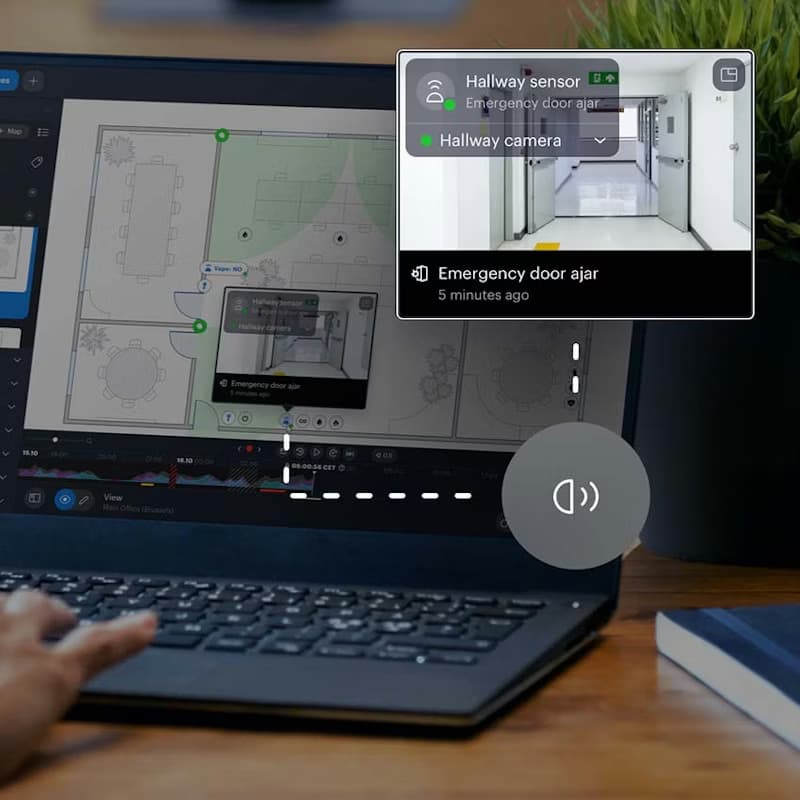
Siloed IT and security create compliance gaps that are hard to detect and harder to defend. In 2026, auditors, insurers, and customers expect provable, enforced controls, not fragmented ownership.
IT Compliance Management in Los Angeles How California Businesses Build Provable Security Without Vendor Sprawl

This article breaks down what IT compliance management really means, what organizations must be able to prove, and how BTI helps build audit-ready security without unnecessary tools or vendor sprawl.
The Hidden Costs of Physical Security Downtime

Physical Security Downtime causes hidden operational, financial, and compliance risks. Learn the true business impact and how to prevent costly outages.



