Cybersecurity control requirements have increased dramatically due to the spread of cloud and premise-controlled applications, sensors, and apparatuses connected to corporate networks. Controls have the purpose of protecting company and customer information and operations from technology, people’s mistakes, device vulnerabilities, and software security vulnerabilities. At BTI, we help executives see enterprise risk as a single converged problem and solve it proactively.
Whether it’s ransomware, supply chain compromises, OT disruption, IoT vulnerabilities, VoIP exploitation, or physical site breaches, the question every CEO, COO, and CFO must ask is:
What is the liability or impact of an event and how likely it is to occur?
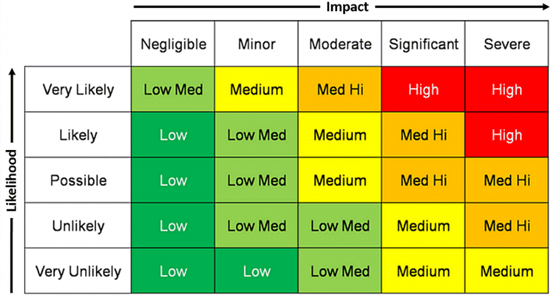
How to Determine the Liability of an Event & How Likely is to Occur
Risk Importance = Impact × Likelihood.
The appropriate analysis and utilization of that formula determines whether an incident is a minor interruption… or a company ending catastrophe.
The NIST 30 Cyber Threats: What Every Leader Should Know
We aligned the official NIST IR 8323r1 list of 30 adversarial threat events, the same framework used in federal and Fortune 500 risk assessments, with practical definitions and controls from major compliance frameworks.
This matrix helps you understand the lingo around threat categories, cybersecurity, and regulatory compliance.
Threat Matrix Overview
Below are examples of some, but not all the key threats from the NIST list and how they relate to standards like:
- NIST 80053 Rev 5
- ISO 27001:2022 Annex A
- HIPAA Security Rule
- CMMC Level 2
- PCI DSS
| Threat Event | Description | Controls/Frameworks Mapped |
|---|---|---|
| Perform Reconnaissance | Attackers gather information on people and systems | NIST 80053, ISO 27001, HIPAA, CMMC, PCI DSS |
| Phishing & Social Engineering | Credential theft via fake emails, vishing, SMShing | Multiple controls across frameworks |
| Ransomware Attacks | Data encryption/extortion | CP, SI Controls; ISO Incident Response |
| Supply Chain Compromise | Third-party exploit entry point | SR, SA controls; ISO supply chain mappings |
| Advanced Persistent Threats (APT) | Longterm stealth intrusions | Zero Trust controls, advanced monitoring |
Why This Matters to Your Business Translating Risk to Liability Exposure
These aren’t abstract risks. They are areas of liability that you face due to your contractual obligations, over 21 State privacy laws, and your industrial regulations. There’s no police force coming to your door to ask you about how you’re managing these risks yet. However, there is an army of plaintiff lawyers and class action plaintiffs making their way to the courthouse steps naming high profile businesses in unregulated and regulated businesses.
Household names that settled cases in 2025 include Meta/Facebook, Google, TikTok, Snap, and Amazon. Lesser-known companies that settled such cases were Samsara (fleet management), Incode (biometrics), Cerebral (telehealth), Rayus Radiology (radiology services), and Lash Group (healthcare).
Whether you operate in:
- Manufacturing
- Healthcare
- Finance
- Energy/OT environments
- Professional services
- Retail or logistics
BTI’s enterprise-wide approach ensures:
- IT & Cloud are protected, not isolated
- Operational Technology (OT) is secured against mission critical disruption
- IoT devices don’t become access points
- Physical Security is integrated into your risk profile
- VoIP & communications are resilient
- Supply chain partners don’t become liabilities
We evaluate risk beyond technology across operations, legal exposure, and reputational impact.
How Our Risk Assessments Work
Assessment & Roadmap:
- Executive interviews and risk clarification
- Documentation of vulnerabilities and threat exposure
- Prioritized mitigation roadmap
Implementation & Controls:
- Remediation planning
- Compliance alignment (ISO 27001, HIPAA, PCI, CMMC)
- Ongoing support options
BTI is a fully licensed, insured, ISO 27001 compliant, and ISNetworld certified converged security integrator serving businesses across multiple states. We are uniquely positioned to provide enterprise risk management that aligns IT security, physical security, compliance, and business resilience.
NIST 30 Cyber Threats & Risk Matrix
Source: NIST IR 8323r1 Appendix B — mapped to major compliance frameworks
Ready to Shield Your Business?
Schedule your free confidential consultation with BTI today
Frequently Asked Questions
What are the NIST 30 cyber threats?
They are adversarial threat event categories from NIST IR 8323r1, baseline examples of real-world attacks that define what organizations should protect against.
Are these tied to compliance frameworks?
Yes, each threat can be mapped to controls from NIST 80053, ISO 27001 Annex A, HIPAA, CMMC, and PCI DSS, helping you align risk, security, and regulatory requirements.
Does BTI assess only IT risks?
No, we provide a converged enterprise assessment spanning physical security, OT, IoT, VoIP, cloud, and third-party exposure.
Who should attend the consultation?
Business executives responsible for strategic operations (CEOs, COOs, CFOs) plus key stakeholders as needed.
How long does a full engagement take?
Typically, 2–4 weeks for a complete assessment and plan; controls implementation follows over the next 30–60 days








