In the healthcare industry, the safety and security of patient information and physical spaces are crucial. Healthcare professionals and facility managers grapple daily with the dual challenge of protecting sensitive data and ensuring the safety of their premises. The treasure trove of personal information and the presence of valuable assets within these facilities make the healthcare industry one of the primary targets. But do not worry, there are ways to keep your valuable data, patients, caregivers, and visitors secure.
Access control systems paired with effective hospital access control policies are a robust solution designed to resolve these security pain points efficiently, ensuring that healthcare institutions can focus on what they do best—saving lives and promoting health.
What are Healthcare Access Control Systems?

At its core, an access control solution is a system that manages entry to physical and digital spaces. In healthcare settings, this translates to controlling who can access certain areas within a hospital or who can view and use patient information stored electronically. Hospital access control systems ensure that only authorized personnel have access to sensitive areas and information, effectively minimizing the risks of unauthorized access and potential security and data breaches.
Types of Access Control Systems for Hospitals
There are multiple types of access control systems for hospitals, each with its unique applications in the medical field. These include:
- Physical Access Control
- Logical Access Control
- Role-Based Access Control
- Mandatory Access Control
- Attribute-Based Access Control
Physical Access Control
Physical access control systems restrict entry to physical spaces within a healthcare facility, safeguarding areas that store sensitive information or assets. Hospital access control systems are often seen at entry points to patient records rooms, medication storage areas, and equipment rooms.
Logical Access Control
Focusing on digital barriers, logical access control regulates who can access electronic healthcare systems and data. Common methods include authentication techniques like usernames, passwords, and multi-factor authentication (MFA). A prevalent model of logical access control systems for healthcare is Role-Based Access Control (RBAC), which assigns specific permissions to users based on their job roles within the healthcare organization.

Role-Based Access Control (RBAC)
RBAC is particularly beneficial in large healthcare settings where each team member’s access needs vary drastically. This model allows for the granular assignment of access rights, ensuring that individuals can only access information or areas relevant to their roles, thereby enhancing the security structure of the entity.
Mandatory Access Control (MAC) and Discretionary Access Control (DAC)
While MAC uses predefined security policies to dictate access based on classification levels of data and users, DAC places the power in the hands of the data owners to set permissions. MAC’s stringent control is suitable for high-security areas, whereas DAC’s flexibility can aid in collaborative environments but requires meticulous management to mitigate risks.
Attribute-Based Access Control (ABAC)
ABAC stands out for its dynamic nature, considering multiple attributes (e.g., user role, location, time) to grant access permissions. This fluidity makes ABAC ideal for healthcare settings where access requirements can significantly vary based on context, such as granting a specialist temporary access during a specific consultation period.
The Benefits of Hospital Access Control Systems
Increased Data & Patient Record Security
With stringent healthcare regulations such as HIPPA, The Joint Commission, and Environment of Care hospitals and healthcare centers must employ proven and reliable methods to safeguard data. Hospital access control systems provide a robust solution, helping these entities fulfill their legal and ethical obligations to patients by preventing unauthorized access to sensitive information.
Improved Physical Security Measures
Beyond data, the physical security of facilities is crucial. Healthcare access control solutions enforce restricted access to drug storage, equipment rooms, and sensitive areas like ICUs and maternity wards, thereby enhancing overall security.
In addition, these systems can be integrated with alarms and locking mechanisms to reduce theft and unauthorized entry risks effectively while creating a streamlined and secure security system that protects visitors, caregivers, and staff alike.
Increased Efficiency
Access control systems contribute significantly to operational efficiency by managing room occupancy and availability. These systems streamline resource allocation and scheduling, ensuring that hospital spaces are utilized optimally. Integration with electronic health records and scheduling software further boosts productivity, allowing for seamless patient flow and room turnover.
The Challenges of Healthcare Access Control Systems
Avoiding “One-Time” Access Privileges
Temporary permissions can quickly become long-term vulnerabilities. Granting single-use or short-term credentials without proper expiration controls opens the door to breaches. Automated access expiry and identity verification prevent unauthorized re-entry and ensure privileges remain time-bound and traceable.
Adjusting Role Changes and Staff Privileges Regularly
Hospitals experience constant staff movement, from rotating nurses to new contractors. Without continuous role-based access updates, former employees may retain access longer than intended.
Effectively Managing Vendors
Contractors, technicians, and delivery teams require access but present unique security challenges. Vendor-specific credentials, audit trails, and time-bound access windows help healthcare facilities maintain compliance and control without slowing down operations.
True security doesn’t operate in silos. Integrating access control with video surveillance, intrusion detection, and alarm systems creates a unified defense strategy. BTI’s solutions enable real-time incident response — when a door is forced open, cameras auto-focus, alerts trigger, and logs are instantly created for investigation and compliance.
How Do Healthcare Access Control Systems Improve Security & Compliance?
Securing Controlled Substances at Hospitals
Pharmacy and medication storage areas are prime targets for diversion. Access control systems restrict entry to authorized personnel, create real-time logs, and provide an auditable trail for DEA and Joint Commission compliance.
Running Audit Trails and Operational Reports
Automatic reporting tools generate detailed access records are invaluable for compliance audits and investigations. BTI systems provide secure data retention and customizable reporting that meets HIPAA and Environment of Care documentation standards.
Providing Proof of Industry Compliance
Regulatory compliance isn’t just a checkbox, it’s a trust factor. Integrated access control provides verifiable logs of access history, training status, and credential activity, making audits smoother and accountability airtight.
Mitigating Cyberthreats
Physical access control is a frontline defense against digital intrusion. By tying physical identity to network access, access control for hospitals help prevent unauthorized device use and strengthen the cybersecurity perimeter, protecting both patient data and hospital networks.
Best Practices for Effective Hospital Access Control in Healthcare
Assigning Role-Based Permissions
Ensuring the right people have the right access is one of the simplest ways to strengthen security. Each employee should only be able to access the systems and data required for their job function, nothing more, nothing less. This “role-based access” approach reduces the risk of data leaks, insider threats, and costly compliance issues. BTI streamlines this by integrating with your HR systems and automating user provisioning, so when employees are hired, change roles, or leave the company, their permissions are updated automatically and consistently across your environment.
Enforcing Robust and Comprehensive Security Policies
Clear, enforceable security policies are the foundation of any effective protection strategy. Without them, even the best technology is underused or misconfigured. Organizations need documented standards for passwords, user access, incident response, data handling, and device usage, and they need to ensure those policies are actually followed.
Regular reviews, audits, and staff training help keep policies aligned with evolving threats and regulatory requirements. Backed by reliable technology, these policies don’t just “exist on paper”, they actively shape behavior and support a strong, resilient security culture.
Implementing Cloud Based Management
Cloud-based management gives security and IT teams a single pane of glass to monitor and control systems from anywhere. For multi-campus hospitals and healthcare networks, this means administrators can manage doors, cameras, intercoms, and alarms across all locations without being physically on-site.
Centralized cloud access improves uptime, simplifies updates, and makes it easier to roll out consistent security policies. The result is a more flexible, scalable security posture that can adapt quickly to staffing changes, expansions, or new compliance demands.
Integrating your Whole Security Ecosystem
When cameras, alarms, access control, and intercom systems operate in silos, critical details can be missed in the moment that matters. BTI connects these technologies into a single, integrated security ecosystem. Events from one system—like a forced door or triggered alarm—can automatically pull up relevant video, notify the right staff, and log activity for reporting and compliance.
BTI’s end-to-end security system integration delivers real-time situational awareness, accelerates response times, and gives security teams a unified interface to manage everything more efficiently.
Implementing Different Access Methods Depending in Different Areas
Not every door in a healthcare facility carries the same level of risk, and your access methods shouldn’t treat them as if they do. Public areas like lobbies or waiting rooms may only require basic access controls, while high-risk zones such as pharmacies, data centers, labs, and medication rooms demand stricter verification.
BTI designs layered access solutions that match each department’s risk profile. This can include traditional card readers, mobile credentials for staff smartphones, PIN codes, and advanced options like biometric verification (fingerprint, facial recognition, or iris scan) for the most sensitive areas.
By combining multiple methods where needed, organizations can balance strong security with everyday convenience, reducing the risk of unauthorized access while keeping clinicians and staff moving efficiently.
Hospital Access Control Applications in Real Healthcare Scenarios
Prohibited Substance Management
Did you know that 70% of medication tampering, fraud, and theft occur in hospitals? (Food and Drug Administration). With thousands of employees, visitors, and caregivers visiting healthcare facilities daily, keeping track of substances can be difficult. Access control in hospitals boosts your substance and visitor security by digitally controlling and monitoring access to restricted areas and resources, allowing you to reduce the likelihood of theft, misuse, or misplacement of controlled substances.
Meeting Security & Compliance Standards
In the healthcare industry, meeting industry compliance requirements is critical to achieving success. Staying compliant with regulations like HIPPA, Environment of Care, and The Joint Commission is not an easy task, but hospital access control systems can relieve some of the pressure of meeting compliance by automating tasks and protecting your most valuable assets.
For example, our healthcare clients not only take advantage of access control to protect and monitor who enters their premises. Our clients leverage healthcare access control solutions and security system integration to maintain PHI (Patient Health Information) safety and allow only authorized personnel to see sensitive information based on their specific permissions and credentials.
Fighting Cybercrime
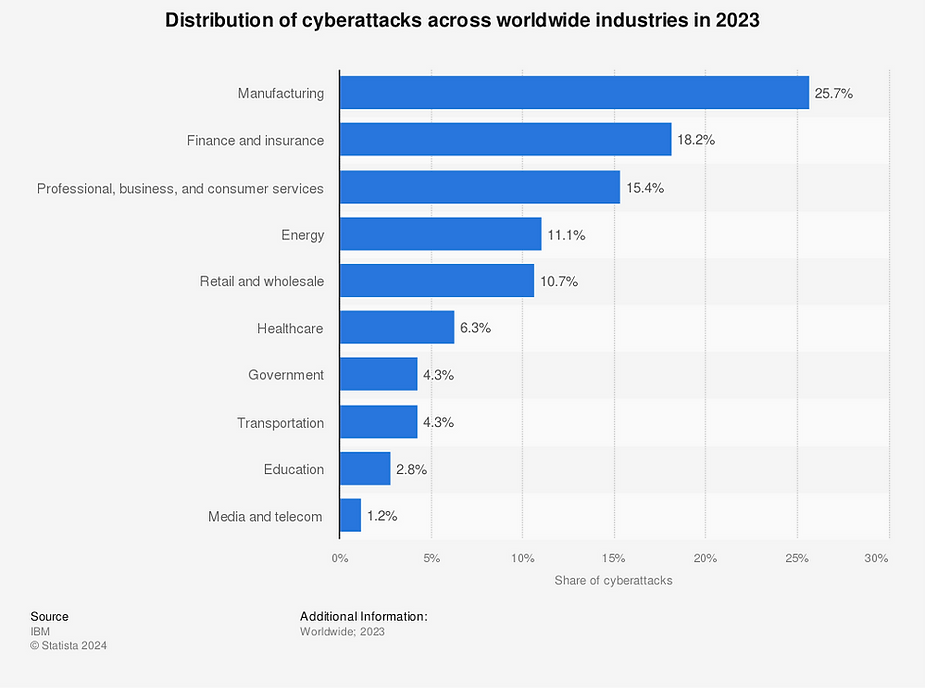
According to a recent IBM X-Force 2025 Threat Intelligence Index, the healthcare industry is one of the industries targeted by hackers worldwide. Data such as employee credentials, employee records, and medical data are some of the most profitable pieces of information on the market, allowing bad actors to make not thousands but millions of dollars by collecting ransoms or selling the information on the dark web.
To fight cybercrime, access control in hospitals comes equipped with advanced security mechanisms such as advanced encryption, authentication technologies, and encrypted access cards.
Running Audit Trails
Implementing access control systems in hospitals and medical facilities offers a straightforward way to secure sensitive areas and quickly spot any unusual or unauthorized actions, whether they originate from internal or external sources. When integrated with other solutions such as video surveillance, hospital access control solutions can leverage both video surveillance and access control to get detailed reports of the systems logs supported by video footage.
This means that if someone swipes their card in any restricted area you will be able to see who swiped the card while receiving visual confirmation from your security cameras to ensure the credentials match with the camera footage and easily identify any breaching attempts by outsiders or scammers.
Get End-to-End Security Solutions with BTI
Hospital access control systems are not a luxury, but a necessity if you want to succeed in the healthcare landscape and comply with the medical industry regulations. The multifaceted approach to security and efficiency provided by healthcare access control systems can significantly mitigate security risks, ensuring the safety of patient information, your premises, visitors, and staff.
The evolution of healthcare access control systems promises even greater capabilities, heralding a future where healthcare security is more robust, responsive, and aligned with the vital mission of health institutions worldwide.
At BTI Communications Group, we understand that healthcare security is about more than just locked doors — it’s about protecting life, privacy, and trust. Our integrated hospital access control systems combine cutting-edge technology with decades of security expertise to deliver peace of mind, operational efficiency, and full regulatory compliance.
Whether you’re upgrading a single facility or securing an entire healthcare network, BTI provides consultation, design, implementation, and 24/7 managed support to ensure your systems stay reliable, compliant, and future-ready.
Strengthen Security & Simplify Compliance with Hospital Access Control
HIPAA, Joint Commission, and state regulations demand more than basic locks and badges. BTI designs, deploys, and supports integrated healthcare access control systems that protect PHI, restrict high-risk areas, and give you clear audit trails for every credentialed entry.







