Today’s threats are smart, persistent, and always looking for the weakest link. Ransomware, phishing, zero-days; they don’t come to you one at a time, and they don’t wait for your IT team to catch up. Hence, one firewall isn’t going to cut it. And neither will be hoping your antivirus catches everything.
That’s why smart businesses are shifting to multi-layered security; a strategy that stacks defenses like firewalls, endpoint protection, access control, identity management, and threat detection to catch what others miss.
BTI designs multi-layered security systems that do more than alert you. They actively stop attacks, integrate IT and physical systems, and are backed by real engineers, not outsourced support.

What Does Multi-Layered Security Actually Look Like?
Think of your network like a fortress. One guard tower won’t stop an army, but multiple barriers? That’s a different story. Each layer catches what the others might miss.
Here’s how BTI builds it:
Perimeter Defense: Firewalls, VPNs, and secure gateways stop unauthorized traffic before it reaches your core network.
Endpoint Protection: Antivirus, EDR, and vulnerability management protect your devices from becoming entry points.
Identity & Access Management: MFA, SSO, and RBAC help enforce who gets in and what they can touch.
Monitoring & Detection: BTI’s in-house SOC uses SIEM and threat intelligence to detect anomalies and respond 24/7.
Physical Integration: BTI integrates access control, cameras, and facility sensors with your IT stack for unified threat visibility.
An example of what we do for healthcare environments is that we link EHR access to building entry points, flagging logins from users who hadn’t physically entered the clinic. This simple integration stops potential breaches.
Layered security isn’t just safer; it’s smarter. At BTI, we like to make it practical for businesses that need real protection, not more stress.
Why SMBs Are Vulnerable Without Multi Layered Network Security
Cybercriminals no longer “work their way up” to big enterprise targets, they go where the defenses are weak, and for many SMBs, that means limited security, limited staff, and no layered protection.
Why? Because most SMBs are under-protected, under-staffed, and overwhelmed by IT demands. Hackers know that one unpatched laptop, one weak password, or one missed alert can open the floodgates.
According to Verizon’s 2025 Data Breach Investigations Report, over 60% of breaches involve SMBs usually due to weak passwords, unpatched systems, or phishing. Hackers know one missed layer can open the floodgates.
And here’s the problem: most SMBs rely on a few disjointed tools; maybe a firewall here, antivirus there, but no integrated strategy. That leaves massive blind spots.

Without multi-layered security:
- A single click on a phishing email can give attackers full access.
- Laptops become entry points without endpoint detection.
- No SOC means threats go unnoticed for days or weeks.
For BTI, bringing structure to the chaos is vital. We integrate perimeter, endpoint, physical, and cloud defenses; customized for your environment, with real engineers monitoring it all 24/7. You’re not just protected, you’re supported.
What to Think About Before Building Your Security Stack
Think of your cybersecurity as a building: the foundation needs to be solid, and each floor adds strength, visibility, and protection. Before you rush to buy another security tool, stop and ask: Do I have the foundation right?
Don’t stack tools, build a security pyramid. BTI’s multi-layered cybersecurity pyramid was designed with one goal; to help SMBs go from reactive survival to proactive security maturity.
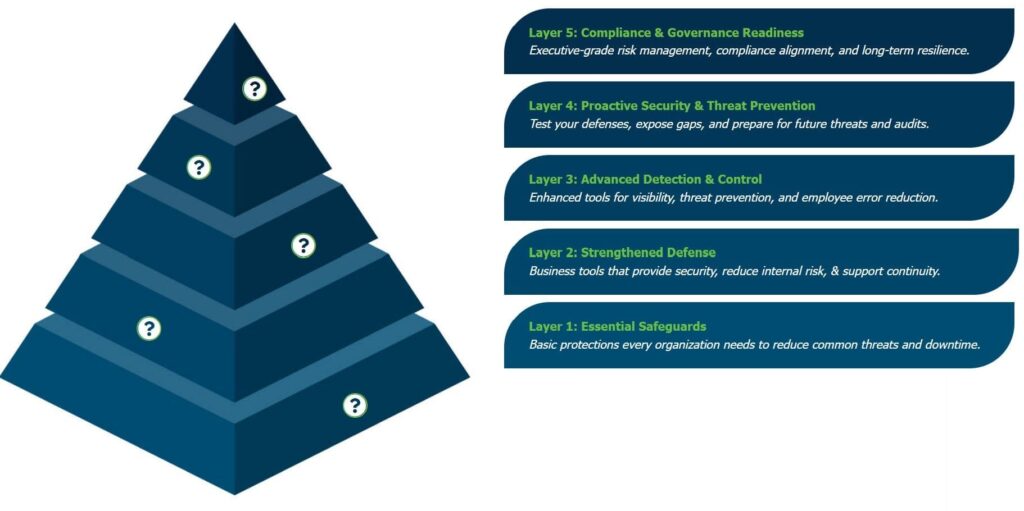
Let’s break it down:
Layer 1: Bare-Minimum Must-Haves
Think of this as your front door lock. Firewalls, MFA, patching; BTI makes sure none of the obvious holes are left open.
Layer 2: Proactive Defenses
Encrypted backups. DNS filtering. Email threat protection. BTI makes sure your team doesn’t click the wrong thing; and if they do, your data survives it.
Layer 3: Intelligent Threat Response
EDR, dark web alerts, phishing simulations. Security moves from passive to intelligent; and BTI’s 24/7 team sees it all.
Layer 4: Business-Ready Visibility
Real-time dashboards. SOC + SIEM integration. Compliance tracking. Now you’re not just protected; you’re informed about what’s going on behind the scenes.
Layer 5: Executive Strategy
We help you build out a full risk roadmap with CISO support, vendor assessments, and future-proof planning.
We don’t just offer tools, at BTI we provide a security roadmap built for outcomes. Each layer builds on the last, starting with essentials that prevent avoidable breaches, and rising to advanced visibility and business resilience.
Who Benefits from Multi-Layered Cybersecurity?
Many businesses still assume a firewall or antivirus alone is enough, but today’s threats bypass those defenses easily. That’s why a layered approach is now considered the gold standard.
Here are some of the industries where we have built custom defenses that integrate physical, digital, and operational security, always backed by real engineers and real outcomes:
Healthcare
Protect PHI, secure connected devices, and stay HIPAA-compliant with layered defenses; from endpoint protection to encrypted backup and SIEM.
Manufacturing
Segment networks, isolate OT environments, and stop threats before they hit the production floor. We defend IoT, IP, and industrial control systems with firewalls, VPNs, and centralized monitoring, no downtime allowed.
Logistics & Warehousing
From facility access control to VPN-secured connectivity across sites, we help you track inventory in real time and protect facility data across multiple locations; without sacrificing speed.
Public Sector & Government
Municipal IT teams need scalable protection. We support city networks, police departments, and public offices with scalable, compliant, gap-free security solutions.
Corporate and Multi-site Enterprises
We make it easy to secure users and devices at every site, unify security across branches, streamline reporting, and get a clear view of your entire security posture.

What to Look for When Hiring a Multi-Layered Security Provider?
Choosing a security partner isn’t about checking boxes. It’s about building a long-term relationship with a team that knows how to scale, integrate, and protect your business at every layer.
From foundational essentials to high-level threat intelligence, here’s what matters most:
True Multi-Layered Security
Ask what’s under the hood. Is it just antivirus and VPNs? Or are they giving you encrypted backups, device control, phishing tests, and web filtering? (Hint: you want the second one.).
A real provider doesn’t stop at firewalls or endpoint protection so look for layered coverage from DNS filtering, endpoint detection, and secure backups to encrypted email and phishing simulations; just like BTI’s 5-layer security framework.
Specialized Expertise
Many vendors resell tools and walk away. You need a security provider that brings actual humans. For example, BTI’s in-house team includes network engineers, SOC/NOC staff, and compliance advisors; all under one roof.
Clear Data & Performance Insights
Layered security is only useful if you can see it working. You need clear insights, logs, and executive-ready summaries; not just a blinking alert. If they can’t show you what they’re protecting (and what they’re not), how can you make decisions?
A Deep Understanding of Compliance Requirements
HIPAA? CMMC? PCI? If you’re in healthcare, manufacturing, or public sector, you must have a partner who understands what those entail. A provider like BTI doesn’t just help you meet regulations; we help you prove it when it matters most.
24/7/365 Support
True layered security evolves. You need a partner that helps you adapt, test, and stay one step ahead — not someone who disappears after setup.
BTI: The Right Partner for Building a Resilient, Multi-Layered Security Strategy
Cybersecurity that’s just “good enough” isn’t good enough anymore. You need a partner who understands your risks, your growth, and your day-to-day chaos and builds security around that.
From foundational safeguards to advanced detection, our multi-layered security approach is based on BTI’s proven 5-tier security pyramid; a framework built to help SMBs move from survival to full control.
Other providers may offer tools. We offer outcomes. You get a custom, scalable solution that’s integrated across your endpoints, users, cloud platforms, and physical access control systems.
One missed layer can cost millions. The average breach now costs $4.45M (IBM 2025). Layered protection isn’t optional. BTI helps you close every gap.
Some final notes, think about these as ‘musts-haves’ and/or non-negotiables, which you’ll be getting by partnering with BTI:
- Full-stack protection
- NOC/SOC + engineering support
- Custom solutions for healthcare, manufacturing, logistics, and more.
Ready to Move from Survival to Proactive Security?
Let’s build your multi-layered defense today.







