
Since 2004, the President of The United States and Congress had declared October as Cybersecurity Awareness Month. The CISA (Cybersecurity and Infrastructure Security Agency) and the NCA (National Cybersecurity Alliance) lead a collaborative effort between companies like BTI in the IT and security industry and government organizations to raise cybersecurity awareness nationally and internationally!
4 Easy Tips You Can Follow to Ensure Cybersecurity.
- Enable MFA (Multi-Factor Authentication)
- Use Strong Passwords
- Train yourself and your staff to recognize and report Phishing
- Keep your software up to date.
We would be more than happy to help you put these into practice. Want help?
What You Can’t See Hurts You
Most organizations have physical security controls to deter crime but are you protected against what can’t be seen?
BTI can help you with:
- Computers, Servers, Software, and Custom Project Work
- Managed or Co-Managed Desktop Care
- Managed or Co-Managed Server Care
- Managed or Co-Managed IOT / Network Support
- Managed or Co-Managed Cyber Security Operations Center
- Managed or Co-Managed Backup and Disaster Recovery Plans and Systems
Click the Button to Get in Contact with One of Our Experts!


Keeping The La Mesa-Spring Valley School Districts Safe
Thank you, La Mesa-Spring Valley School & the Department of Education in the state of California for trusting BTI and hiring us to implement access control at 19 schools in the District. Protecting and securing the environment for the next generation of American leaders is a privilege.
Click below for more information on BTI’s Federal and State Contracts
Hackers Release LAUSD Data After Supt. Alberto Carvalho Refused to Pay Ransomware
The damage from the leaked data, liability for carelessness, and the operational cost of recovering from this hack is yet to be determined. Also of interest is whether anyone within LAUSD will be held to account.
On average, these attacks cost $500,000.00 in operational and financial damage but LAUSD is the second largest publicly funded system in the USA, so we expect expenditures on fixing the problem and paying out settlements to be orders of magnitude higher.
What happened is that hackers released sensitive data stolen in a cyberattack. The data was released on Saturday, October the 1st, two days before the previously given deadline after Carvalho refused to pay the ransom.
Carvalho informed the public on Friday that the district would not pay the ransom demand or negotiate with hackers. There are no specifics on how much was demanded or what information was leaked on the Dark Web.

Complete Security Includes Cybersecurity
A common mistake committed by a large number of organizations is not including cybersecurity measures or only half-baked measures in their security plans. In order to ensure the complete protection of any business or organization cybersecurity needs to be included.
A lack of good cybersecurity measures will give affect your business by bringing you
- Economic costs : Theft of intellectual property, sensitive corporate information, costs of repairing damaged data systems, and more.
- Reputational costs : Loss of consumer trust, loss of current and future consumers due to lack of cybersecurity, poor media coverage, and more.
- Regulatory costs : Your organization will suffer from regulatory fines and sanctions if you fail to comply with cybersecurity laws.
If you would like to boost your physical and digital security measures contact us now and schedule a free assessment!

Do More/ Pay Less
Are you tired of getting unrecognized charges on your business phone bill, extra hidden cost, and poor-quality service? If you are looking for a reliable low-cost voice solution that allows you to pay only for what you use, GoodPhone is for you!
Meet Crown Fence
Crown Fence Company is one of the largest fence contractors, fabricators, and wholesalers, serving all of California since 1923. We recently had the opportunity to work with Crown Fence, this is the experience of Mr. Patrick Fiedler, General Manager of Crown Fence.
“Before contacting BTI we didn’t have constant tech support, we were experiencing server issues, internet domain issues, email issues, and a lot of IT-related questions that needed to be addressed.” Mr. Fiedler said.
BTI installed servers, multiple computers, and moved all of Crown Fence IT infrastructure, set up remote logins, and more. “BTI’s service was good, timely, and professional, overall, it’s been good working with BTI, all my expectations were met so far,” Patrick said.
What are you waiting for to experience the IT service that you deserve? Contact us now and schedule a free business assessment!

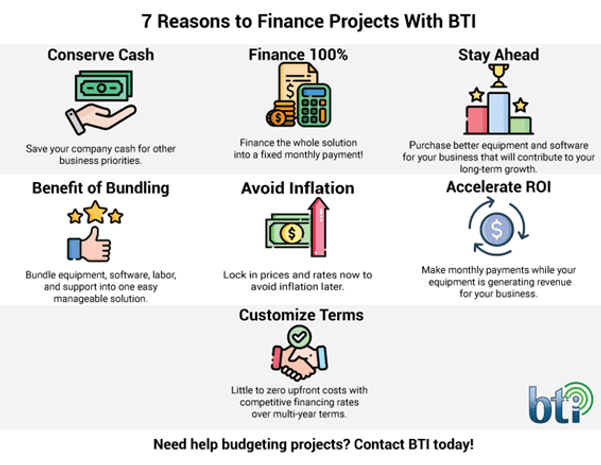
The Benefits of Vendor Financing
Since 1986, BTI has offered special financing for customers interested in acquiring systems or completing projects with BTI. In addition to a lower rate and better terms, BTI’s financing programs offer the following features:
- 100% Financing
- No Down Payment or Personal Guarantee (for established businesses)
- 0-6% Interest Rates
- Fast Approval Without Financial Statements
- 12 to 84-month Terms
- Ability to Bundle Discounted Extended Services and Intangibles to Boost Return on Investment and Lower Costs
Cybercriminals Are Selling Access to Hikvision Surveillance Cameras
According to CYFIRMA research, over 80,000 Hikvision cameras are vulnerable to an 11-month-old command injection flaw. Hikvision, or Hangzhou Hikvision Digital Company, is a manufacturer of video surveillance equipment. Hikvision is present in over 100 countries including the US even though the FCC labeled Hikvision cameras as “an unacceptable security risk” in 2019.
Last fall, the command injection flaw was revealed and named CVE-2021-36260. The exploit was given an astonishing 9.8 out of 10 rating by NIST.
Even though the vulnerability is almost one-year-old, over 80,000 affected devices remain unpatched. Researchers have discovered multiple exploits in Hikvision cameras using the command injection vulnerability. Specifically in Russian, leaked credentials are on sale via dark web forums.

The amount of damage from the Hikvision vulnerability is still unclear. The authors of the report speculate that “Threat Groups such as MISSION2025/APT41, APT10, and its affiliates as well as other actors could potentially exploit this vulnerability to fulfill their motives. (Which may include specific geopolitical considerations).”
The Risk in IoT Devices : In cases like this, it’s easy to blame organizations for leaving their devices unpatched. In this particular scenario, it’s not that simple. David Mayor, Senior Director of threat intelligence at Cybrary, states that Hikvision cameras have been vulnerable for many reasons, “Their products contain easy-to-exploit systematic vulnerabilities or worse, use default credentials. There is no good way to perform forensics or verify that an attacker has been excised. We have not observed any change in Hikvision posture to signal an increase in security within their development cycle.”
Lots of these problems are endemic to the industry, not Hikvision. “IoT devices like cameras aren’t always as easy or straightforward to secure as an app on your phone,” Paul Bischoff, privacy advocate with Comparitech, wrote in a statement via email. “Updates are not automatic, users need to manually download and install them, and many users might never get the message. Furthermore, IoT devices might not give any indication that the system is unsecured and out of date.”
Cybercriminals can scan vulnerable devices with search engines like Shodan or Censys. The problem can certainly be compounded by laziness, as Bischoff noted, “by the fact that Hikvision cameras come with one of a few predetermined passwords out of the box, and many users don’t change these default passwords.”
Nelson, N. (2022, September, 25). Cybercriminals Are Selling Access to Chinese Surveillance Cameras [Blog Post]. Retrieved from: Here
6TB of Sensitive Information Gets Hacked by Mexico’s Secretary of Defense.
Last week a cybercriminal group known as “Guacamayas” hacked the computer system of the Secretary of National Defense (Sedena) leaking more than 6TB of national security documents dating from 2016 to 2022. Mexico is not the first Latin American country attacked by the “hacktivists”. Chile, Colombia, Peru, and El Salvador have also been victims of this criminal organization.
President Andres Manuel López Obrador confirmed the veracity of the attack but did not view the threat with great importance. However, only a small portion of the information has been released, meaning that Mexico will experience a slow drip of document leaks over the coming weeks.

The attack exposed extremely sensitive information including:
- The Poor Health of the Mexican President
- Information on the Failed Military Operation Known as “El Culiacanazo”
- Lack of Security in Mexican Airports
- Internal Discussions Between the Mexican Army and Navy
- Corruption ties between Mexican Politics and the Cartel.
- Monitoring of the US ambassador to Mexico.
- Databases containing sensitive information of deployed military forces in different zones of Mexico
- Information oN Federal Contracts & more.
According to experts, the vulnerability used by hackers to breach the Mexican government was an evolution of “ProxyShell”, a vulnerability in the server of Microsoft Exchange detected in the first semester of the last year. Francisco Solano IT director and portfolio from Logicalis for northern Latin America said:
“Lots of the patches for this vulnerability were published months after it was discovered. When you don’t have the right mechanisms or necessary personnel everything is very complex. We have the antidote, but we don’t have someone to apply it” Solano said.
Ransomware Is an Increasing Cyber Threat in Mexico & The World.
According to a study done by Sophos, from 200 organizations in Mexico, 75% were victims of ransomware. The average ransom paid by these organizations was 500,000 dollars. Just in 2021 ransomware attacks grew 600% in Mexico.
According to multiple cybersecurity experts consulted by Reuters, cyberattacks are going to continue to be more common and government and private industry are both vulnerable all over the world.
To finalize Adolfo Grego a specialist in the forensic investigation said, “There is a deterioration of the defensive postures in terms of cybersecurity. A key aspect of this deterioration is the government’s economic austerity.” Grego said. “Mexico has world-class cybersecurity specialists but the current administration it’s not taking them into account.” He added.
Staff, F. (2022, October 1). Hackeo masivo a Sedena evidencia vulnerabilidad de ciberseguridad; así fue el ataque. Forbes México. Retrieved October 3, 2022, from https://www.forbes.com.mx/hackeo-masivo-a-sedena-evidencia-vulnerabilidad-de-ciberseguridad-asi-fue-el-ataque/





